Opsbeacon
Connections
Connections form the backbone of your OpsBeacon integration, linking your environment to various external systems and resources. These connections enable seamless automation and interaction with platforms such as SSH servers, AWS accounts, databases, APIs, or on-premise worker nodes (Agents). Below is an overview of the supported connection types and their configurations:
Connection Types
1. SSH
The SSH connection links OpsBeacon to remote servers using the SSH protocol. It requires the host address and an SSH private key for secure access.
2. REST
The REST connection is used for communicating with custom APIs. You can define the base URL, specify headers, and select your preferred authorization method, such as bearer tokens, basic authentication, or API keys.
3. AWS
The AWS connection facilitates integration with AWS accounts, allowing OpsBeacon to automate cloud-based workflows. It includes settings like the default region, account ID, and AWS secret key to enable secure access.
4. SQL
The SQL connection is designed to interact with SQL databases for executing queries. Configuration includes specifying the host and port, with credentials securely retrieved from secrets stored in OpsBeacon.
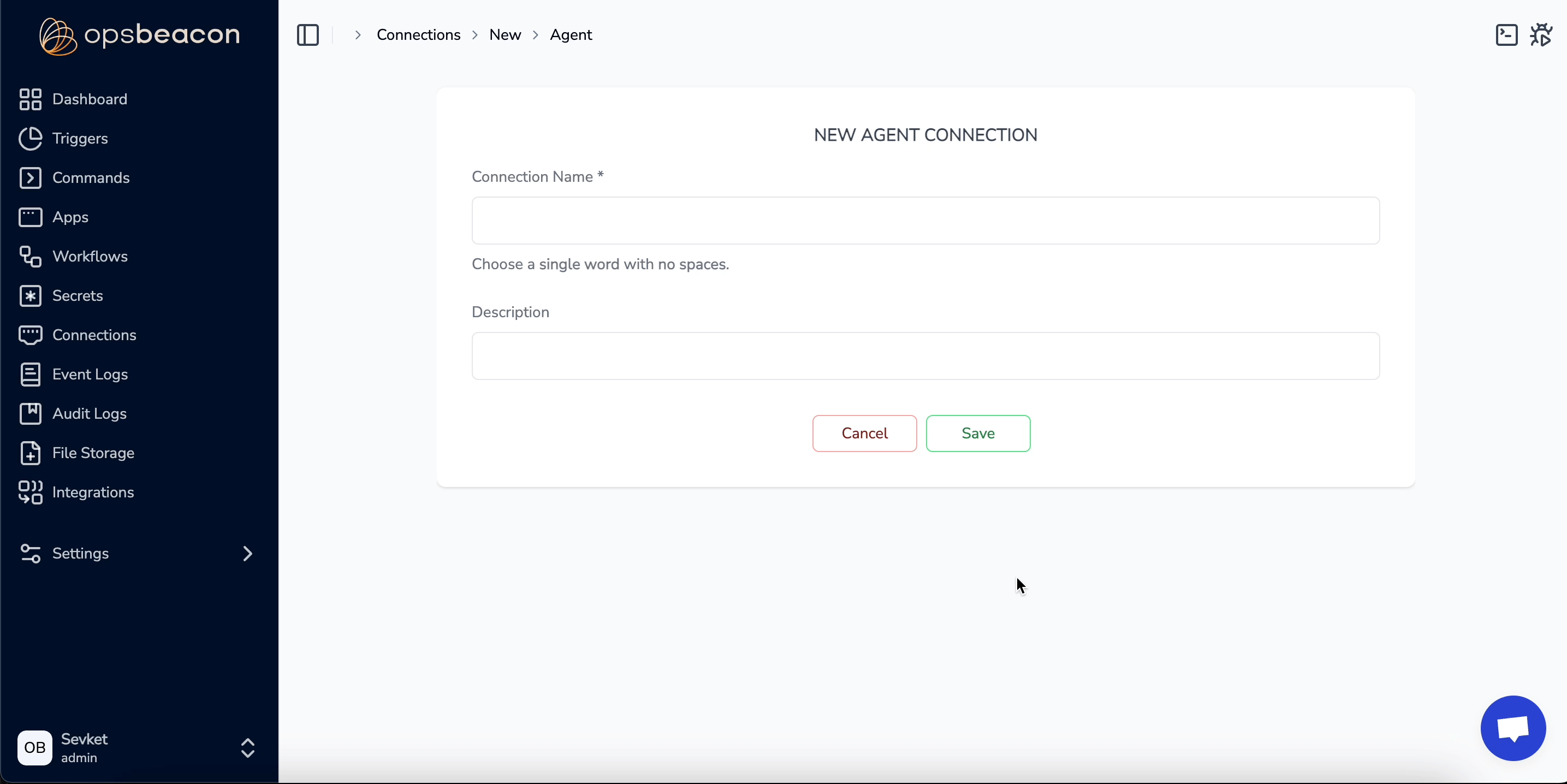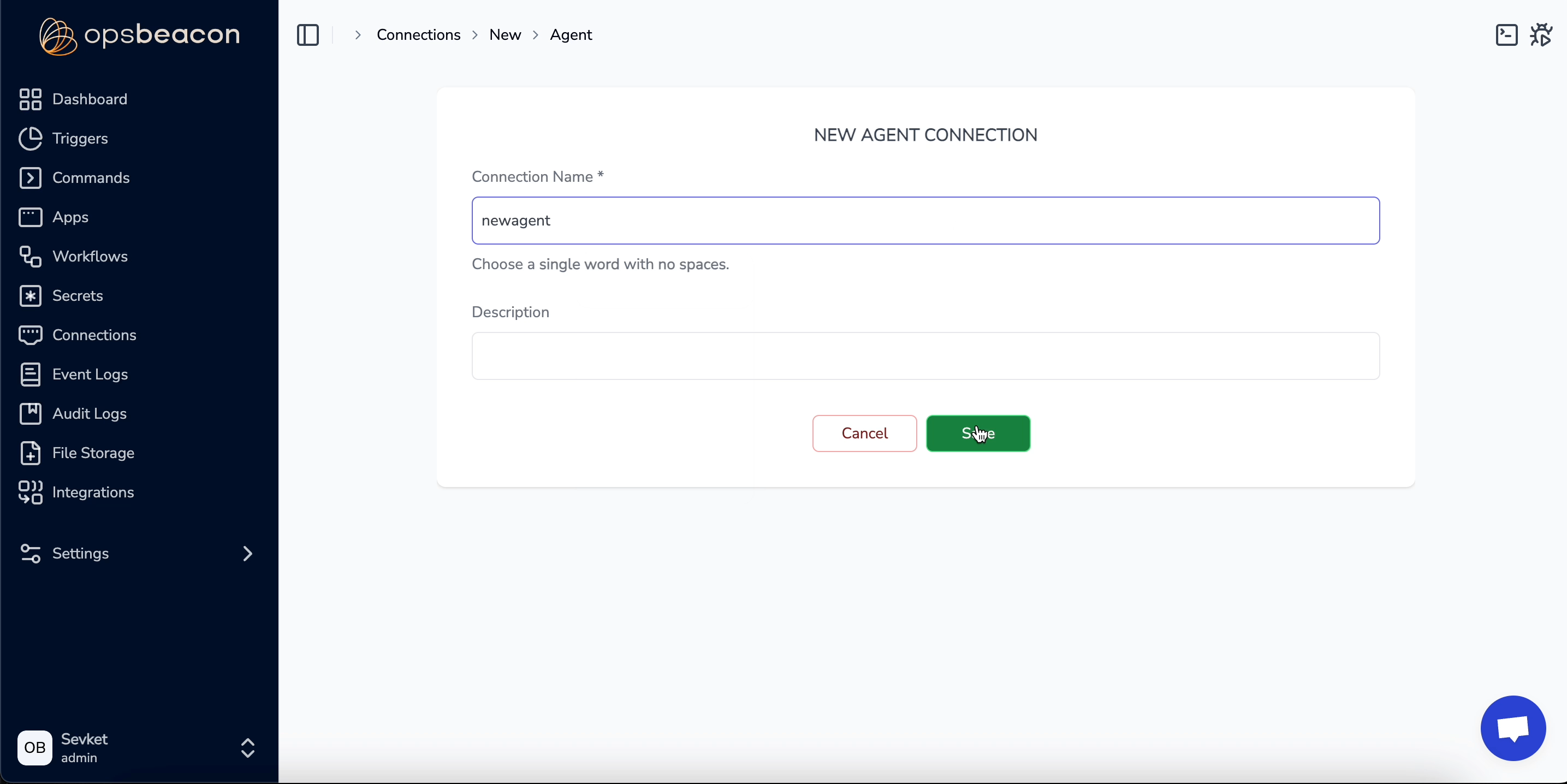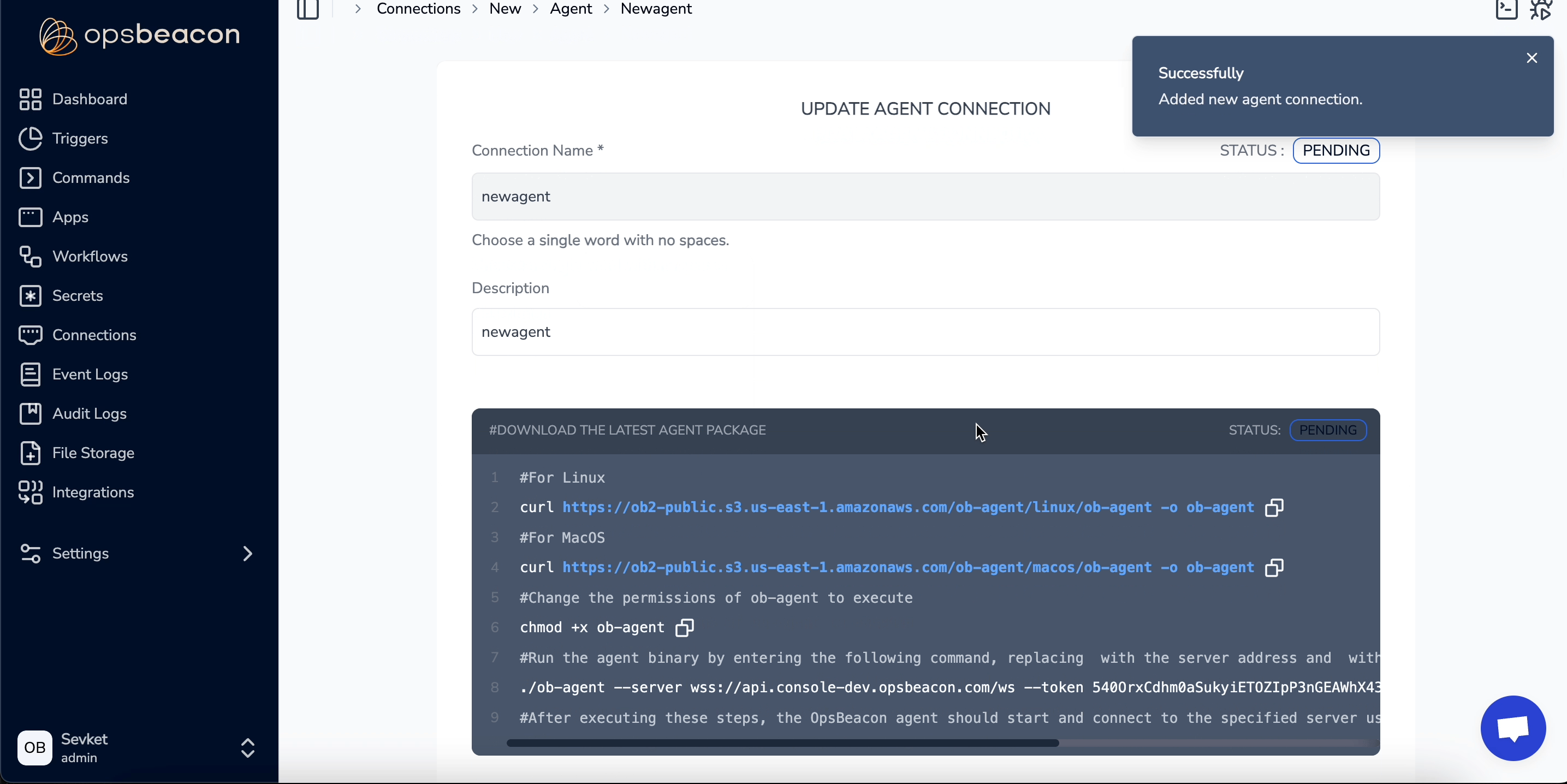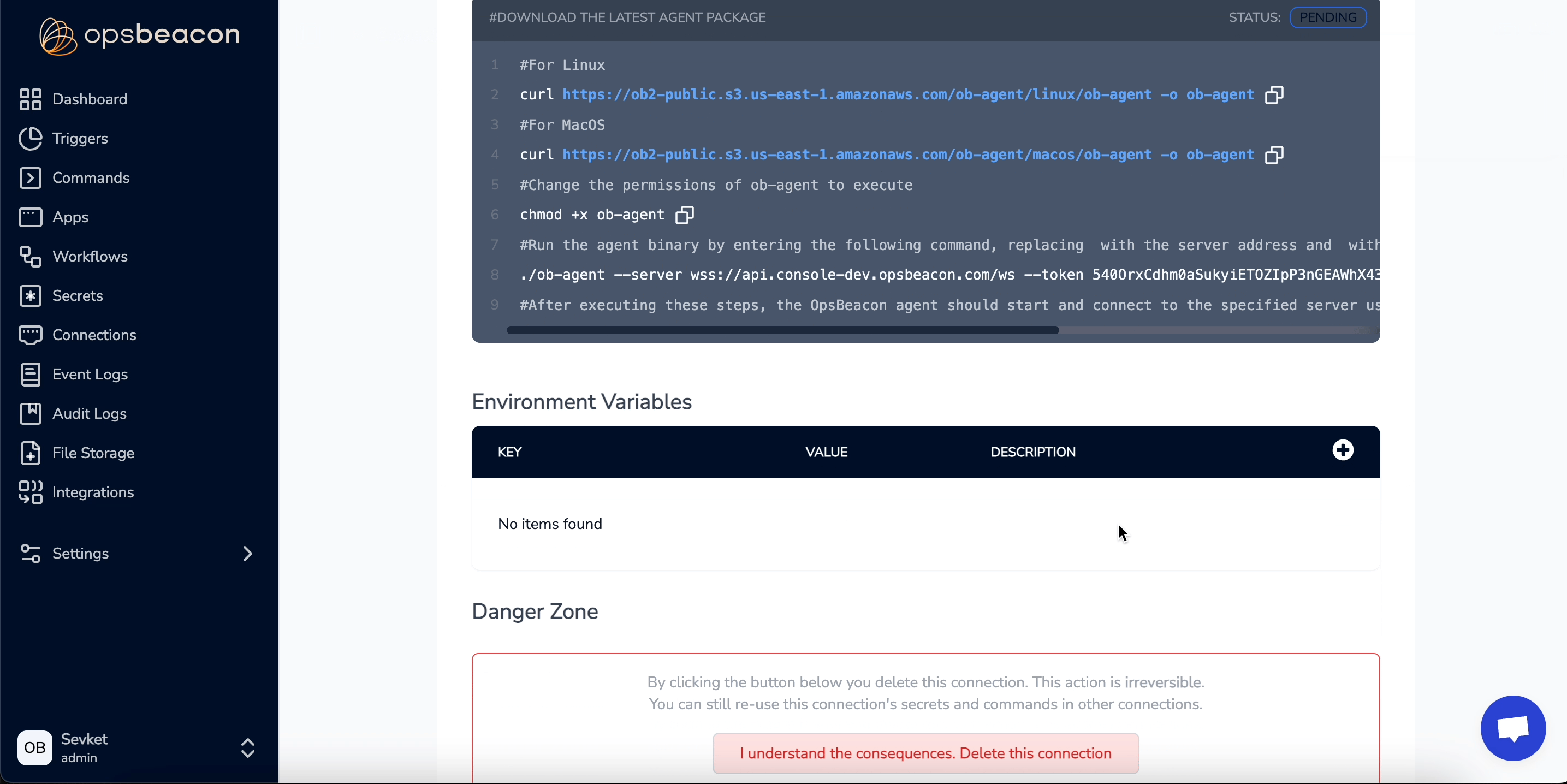
5. AGENT
The AGENT connection acts as a worker node, enabling OpsBeacon to execute tasks directly on your server. Once an Agent connection is created, a download link and installation commands are generated on the setup page. By following these steps, you can configure the agent and run your executions seamlessly.
6. JIRA
The JIRA connection integrates OpsBeacon with JIRA to automate project management tasks. This connection requires the JIRA URL and credentials for secure interaction with the platform.
7. SSM
The SSM connection leverages AWS Systems Manager (SSM) to perform remote executions on EC2 instances. Configuration includes SSM credentials, the target region, and the intended execution target.
Important
If you are using role-based AWS authentication, In addition to this trust policy which will allow OpsBeacon AWS account to assume your role in your account - you also need to provide necessary permissions for us to be able to send SSM Run Commands to your target EC2 instances. Here is a sample permission policy that allows us to execute remote commands on any instance. You can limit this further based on your needs. Refer to AWS documentation
{
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Action":[
"ssm:SendCommand"
],
"Resource":[
"arn:aws:ssm:*:*:document/AWS-RunShellScript"
]
},
{
"Effect":"Allow",
"Action":[
"ssm:SendCommand"
],
"Resource":[
"arn:aws:ec2:*:*:instance/*"
]
}
}
]
}
